📣 Sharing an important story with you all! 💡
My friend and I were working on a project that involved opening a pickle file downloaded from an external website, aiming to create a utility for handling data from that source. This encounter led me to a crucial realization about the safety concerns associated with pickles.
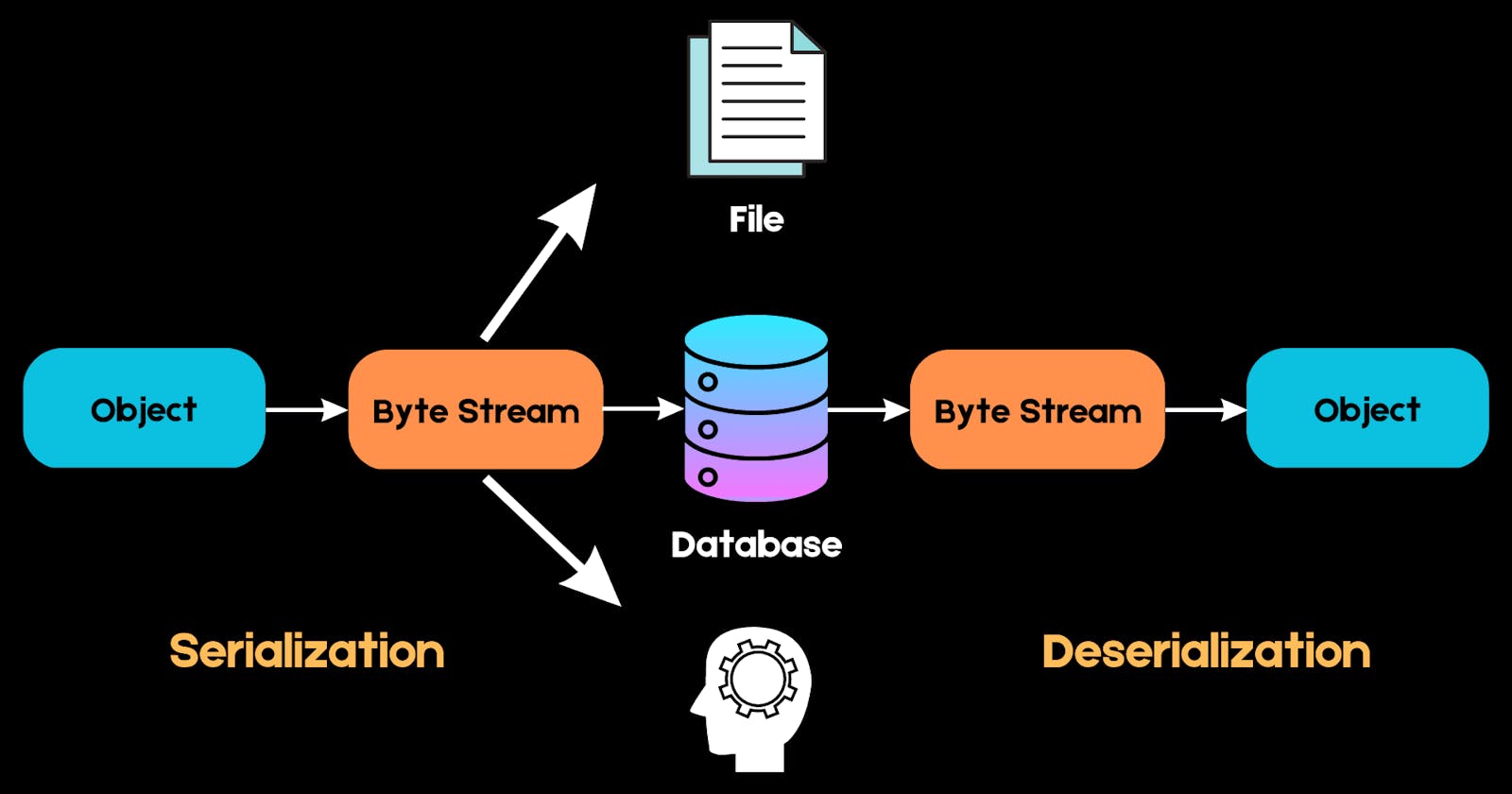
While Pickle can be a powerful tool for serialization and deserialization in Python, it's important to be aware of its potential risks. Pickle poses a security challenge since it allows code execution during the unpickling process. This means that if we attempt to unpickle untrusted data, we open ourselves up to significant vulnerabilities.
Let me emphasize this: There is NO safe way to unpickle untrusted data. It's vital to exercise extreme caution and never unpickle a file that is not your own, especially when dealing with data from external sources.
This experience served as a reminder of the importance of data security and best practices in our project.
Let's dive into a code example to see how this works:
import pickle
def process_data(data):
try:
obj = pickle.loads(data)
# Process the deserialized object
# ...
return obj
except pickle.UnpicklingError:
print("Error while unpickling the data.")
return None
In this code snippet, we have a function called "process_data" that takes some serialized data as input. It tries to convert that data back into an object using "pickle.loads()", which is the unpickling function in the pickle module.
However, the problem arises when the data comes from an untrusted source. Let's say someone sneaky sends you a pickle file, but they've manipulated it in a malicious way. When you try to open and use that file, it could actually execute harmful code on your computer!
This sneaky trick is called a "pickle bomb" or a "deserialization attack." Basically, it means that the unknown sender can hide harmful instructions in a pickle file, and when you try to unpickle it, those instructions get executed. It could lead to all sorts of trouble, like hackers taking control of your system, stealing your data, etc.
To safeguard against these risks, it's crucial to be extra cautious when dealing with untrusted data. If you can't be absolutely sure about the source and integrity of the data, it's best to avoid using pickle altogether. Instead, consider using safer alternatives like JSON or XML, which have built-in protections to prevent such attacks.
In a nutshell, the lesson here is that you can't trust just any old pickle file that comes your way. Unpickling untrusted data is like opening a mystery box with hidden dangers inside. It's essential to be cautious, use safer alternatives, and keep your computer and data secure.
🌟 I would love to hear your thoughts on data security and any experiences you've had with secure coding practices. Share your insights in the comments below!